A critical vulnerability has been discovered in the Python module that is over 15 years old, and as many as 350,000 open source projects are believed to be vulnerable.
Open source code repositories cover a wide range of industries, including software development, artificial intelligence/machine learning, web development, media, and security.
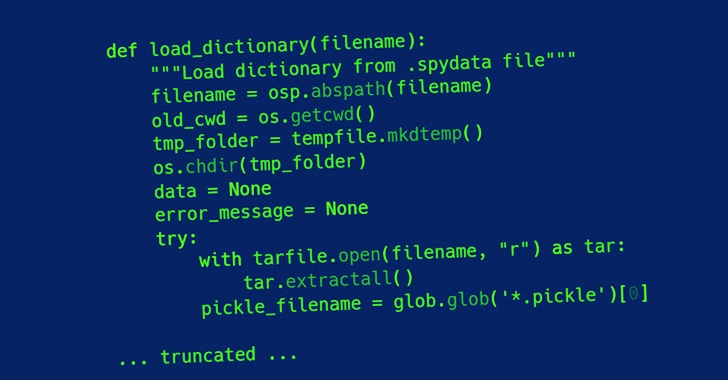
This CVE, known as CVE-2007-4559, has a CVSS score of 6.8 and is found in the tarfile module. If exploited successfully, it could allow for code execution from an arbitrary file write.
“The vulnerability is a path traversal attack in the extract and extractall functions in the tarfile module that allow an attacker to overwrite arbitrary files by adding the ‘..’ sequence to filenames in a TAR archive,” Trellix security researcher Kasimir Schulz said in a writeup.
The bug, which was originally disclosed in August 2007, involves how a tar archive that has been crafted in a specific way can overwrite any files on the target machine just by opening the file.
A threat actor can exploit a system’s weaknesses by uploading a malicious tarfile. This allows the attacker to escape the directory that houses restricted files and access other unprotected areas of code, which could lead to seizing control of an entire device.
The Python documentation for tarfile states, “You should never uncompress archives from untrusted sources without inspecting them first. It’s possible that the files created are outside of the specified path.” For example, this could happen with members who have absolute filenames starting with ‘/’ or filenames containing ‘..’.”
The security breach is reminiscent of another one that was recently disclosed in RARlab’s UnRAR utility (CVE-2022-30333) where remote code execution could occur. Trellix has taken things a step further by releasing Creosote, a custom virus scanning software, to scan for projects vulnerable to CVE-2007-4559. By doing this they were able to discover the vulnerability in both the Spyder Python IDE as well as Polemarch.
“Left unchecked, this vulnerability has been unintentionally added to hundreds of thousands of open- and closed-source projects worldwide, creating a substantial software supply chain attack surface,” Douglas McKee noted.





